Which of the Following Best Describes a Firewall
Which of the following best describes the concept of a DMZ when using firewalls. Which of the following best describes a DMZ.

What Is A Firewall Definition Key Components And Best Practices Toolbox It Security
What do you call a firewall that is connected to the Internet the internal.
. It checks only the IP and protocol. Hardware firewalls can be a standalone product or can also be built into devices like broadband routers. It acts as a gateway for requests arriving from the client.
A It examines each packet against a set of criteria. Serves as a single point of entry to the network. Which of the following best describes the Gramm-Leach-Bliley Act.
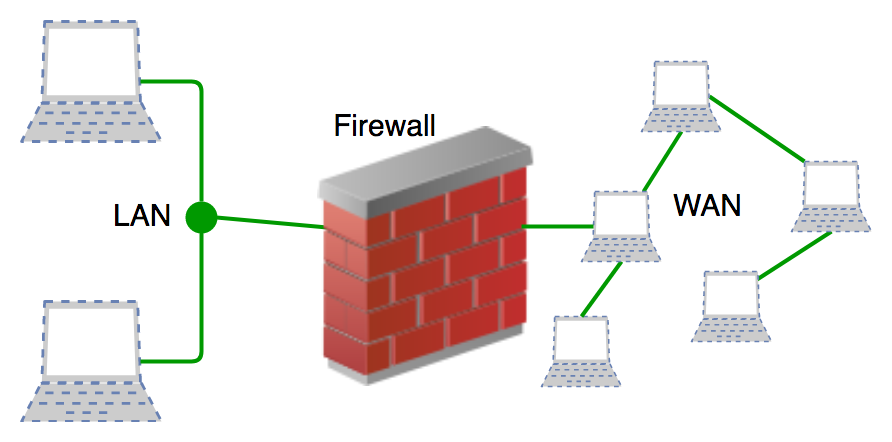
D when a company defrauds its suppliers by making false claims. A firewall is a pass-through device that allows only certain traffic in and out. It is typically run on the host system.
C This is a zone within the proprietary network that needs access from outside the proprietary network. Which of the following BEST describes a firewall. Which of the following BEST describes a firewall.
It sends traffic through another host. Software firewalls are generally used to protect individual hosts. BIt acts as a gateway for.
The current packet but also on data derived from previous packets in the conversation. A device that analyzes traffic based on destination address. B This is the zone outside the proprietary network.
AIt sends traffic through another host. B when two or more people cooperate together to defraud a company. CASB ensures the security policies of the enterprise comply with the cloud.
A load balancing system that acts as a funnel point for traffic that is an ideal place to enforce policy and that is done through the firewall. A subnet of publicly accessible servers placed outside the internal network. Hardware firewalls are physical devices that are usually placed at the junction or gateway between two networks generally a private network and a public network like the internet.
A device that monitors the characteristics of a single host and the events occurring on that host. A proxy installed between a firewall and a web server. A A software and hardware system that prevents outsiders from accessing a companys internal network.
Which of the following best describes a mantrap. A firewall is a network segment off the firewall in which you put systems that require different levels of access than other network components. 4 rows Which of the following best describes a host-based firewall.
Which of the following best describes the cloud access security broker. A a malicious program that enters program code or destroys data without authorization. Which of the following best describes the cloud access security broker.
B A tool that searches Web pages containing the users search terms and then displays pages that match. A host-based firewall is a. A firewall is a software or a hardware device that can filter incoming or outgoing traffic based on certain criteria.
Which of the following best describes a proxy firewall. Which of the following statements best describes a stateful packet inspection firewall. A stateful packet inspection firewall examines each packet and denies or permits access based not only on the current packet but also on data derived from previous packets in the conversation.
Which of the following best describes a proxy firewall. A This is the zone inside the proprietary network. Asked Dec 28 2016 in Computer Science Information Technology by giugiu.
Data must be stored on a secure medium and special security measures must be enforced to protect such data on storage media and during transmittal. You are asked to configure your firewall in such a way that the traffic from source address range 1171121025 through 11711215100 is allowed while traffic from 1171121225 through 1171121325 is denied and traffic from 11711212200 through 1171121310 is. The Gramm-Leach-Bliley Act requires financial institutions to ensure the security and confidentiality of customer data.
A a software and hardware system that prevents outsiders from accessing a companys internal network B a tool that searches Web pages containing the users search terms and then displays pages that match C a private network of internal websites and other sources of information available to a companys employees D. CASB is a virtual alternative to a physical firewall. AIt tracks geographic locations of connections.
C a technique for protecting data. Which of the following best describes a network chokepoint. A mantrap is a small space with two separate sets of interlocking doors.
A mantrap separates threat actors from defenders. BIt prevents TCP traffic from being sent as UDP traffic. A mantrap is a challenge given to cybersecurity experts.
DIt tracks connections from beginning to end. CIt keeps a table of traffic that it must block. CASB secures the data stored in the cloud by restricting unauthorized access.
A mantrap cools a server room by trapping body heat. C It works by examining the client application to determine if traffic is permitted. A firewall is a pass - through device that allows only certain traffic in and out.

This Picture Describes How Does The Internet Works In My Opinion This Is A Great Picture Because It Show How Internet Works Local Dating Sites Internet Dating

Network Firewall An Overview Sciencedirect Topics

Textbook Uses Terminology Like Double Single Bastion Inline T To Describe Firewall Architectures Are These Terms Used In Professional Environments Information Security Stack Exchange
Comments
Post a Comment